FORUM CTRLX AUTOMATION
ctrlX World Partner Apps for ctrlX AUTOMATION
Dear Community User! We are updating our platform to a new
system.
Read more: Important
information on the platform change.
- ctrlX AUTOMATION Community
- ctrlX World Partner Apps for ctrlX AUTOMATION
- Smart HMI - WebIQ Designer and Server
- Re: Web IQ TLS ctrlX Core
Web IQ TLS ctrlX Core
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2022 09:11 PM
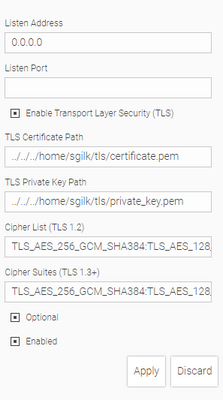
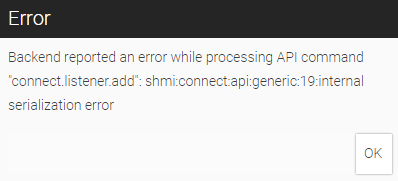
I am trying to add a listener with TLS enabled to the Web IQ runtime on my ctrlX core. I generated the certificate and private key via SSH into the core. I recieve the error below when applying this configuration in Web IQ designer. This is not listed in their API documentation.
Is there a documented method of doing this correctly somewhere?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 06:51 AM
You have to register for the internal aera of SmartHMI web page.https://www.smart-hmi.com/user/download/deliver/docs/documentation-manual-connect-configuration-tool...
Section: TLS Configuration example
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 07:59 AM
A listener needs a listener port - that's how TCP/IP works. In your screen I can see that you don't have a port set.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 03:01 PM
Their documentation states the port is 443 by default. You can specify if you want it different.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 03:02 PM
"Default" relates to port 443 for HTTPS - not as a default port when you enter nothing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 03:04 PM
Hello,
These are the instructions I referenced. I recieved the error message above when configuring via the designer. The command line tools cannot be run from within their snap installation folder on the core. That directory is formatted such that it is read only and cannot be changed by chmod.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 03:37 PM
Your screenshot clearly shows that you did not enter a port number.
If you enter a port number it should work. This is a mandatory field and as such you are getting an error when you leave it empty (albeit not a good one, unfortunately).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 03:55 PM - edited 08-18-2022 03:58 PM
Specifying the port allowed the listener to be added and I can access the page with the specified FQDN as (192.168.100) and using self signed certificate, but I recieve a certificate not valid error and the HMI application is not displayed.
Is there a correct location I should be storing the certificates?
Currently, I have them in a folder in the core /home directory, since I can't place them in the snap folder.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 03:58 PM
Can you please specify what "cannot access" means? Are you getting a timeout in the browser when accessing https://192.168.100/ - or any other error message?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 04:01 PM
Here are some images.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 04:07 PM
Then everything is working correctly from the WebIQ (and probably ctrlX) side. Browsers behave like this if you use a self-signed certificate, that's a security feature and not a bug and happens with any website.
This might help you to find a solution: https://www.google.com/search?q=google+chrome+insecure+self+signed&oq=google+chrome+insecure+self+si...
"Certificate is not valid" might also point to the time not being setup correctly on your ctrlX but you would still get these error messages from any browser.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2022 02:57 PM - edited 08-25-2022 03:11 PM
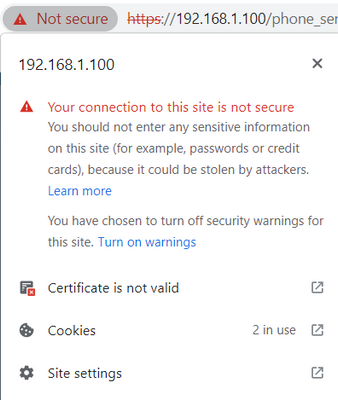
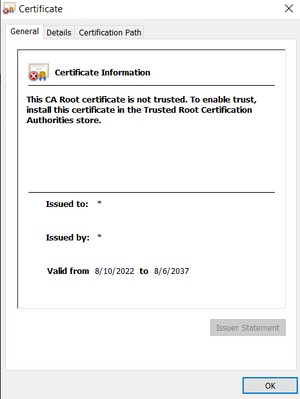
I installed the certificate as trusted in my browser. The page still indicates unsecure and the HMI application is not displayed.
It seems to me these might be separate issues?
I can access the HMI application at the HTTP endpoint, port 10123.
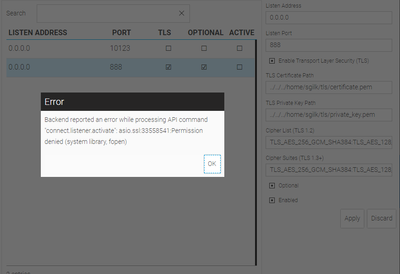
I tried disabling the listener on port 10123 and changing the TLS listener to port 888, in case it was interfering with the ctrlX web interface. I then recieve this error which I can't find in the API reference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2022 08:09 AM
You should never disable the listener on port 10123 as then you won't be able to connect with WebIQ Designer anymore. Just add a new listener on a different port, e.g. port 443 for the standard HTTPS port.
I assume the error occurs because the certificate files cannot be read by WebIQ Server due to a permission issue. Do the files have the correct permissions? If it's related to those files it would rather be a ctrlX and not a WebIQ issue and unfortunately then I cannot help you any further and someone from ctrlX would have to step in here as I don't know how you could change the permissions in ctrlX.
Permissions on the private key files are by default very strict for obvious reasons.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2022 07:19 PM
Do you have a suggestion on someone to contact? This will be an important capability for the ctrlX Core.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2022 08:19 AM
Normally they read this forum as well and I assume they would reply here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2022 08:37 AM
We will check this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2022 02:18 PM - edited 09-15-2022 02:20 PM
Sorry for the late reply.
We had a look to this topic and think that it as a problem because the WebIQ server does not have access to the certificates you uploaded. Please beware of following points:
- Each snap is running in a sandbox and do not have any access rigths to the file system but on his own installation path (e.g. /var/snap/ctrlx-smarthmi-webiq-runtime/current/). See this post for how it looks like in Node-RED.
- Access to other locations has to be granted by e.g. UnixPipes. We do so with our app data (activeConfiguration). But for this a snap plug is needed in the interface of the app that should be able to participate. See this post for how to access from a snap and from a PC to corresponding path "/var/snap/rexroth-solutions/common/solutions/activeConfiguration/".
- A standard ctrlX CORE will have no active SSH connection. Only for testing/development purposes a system user can be handed out by Rexroth that will grant this rights. See this post for further information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2022 04:40 PM
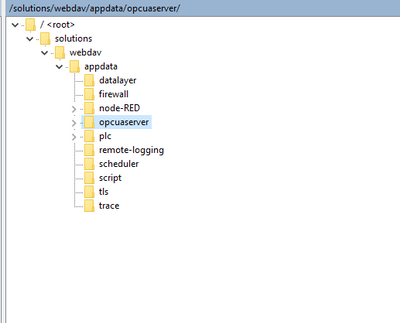
I do not see a configuration folder for WebIQ Server over WebDAV. Does this mean the server app would need to be modified to support upload of TLS certificates?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2023 08:38 AM
Is this still an issue or can this topic be closed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2023 04:34 PM
I was able to activate a listener after packaging the certificate files with the published app. The path to the certificate files is then:
/var/snap/ctrlx-smarthmi-webiq-runtime/current/.webiq/WebIQ Projects/cp_1/TLS/certificate.pem
/var/snap/ctrlx-smarthmi-webiq-runtime/current/.webiq/WebIQ Projects/cp_1/TLS/private_key.pem
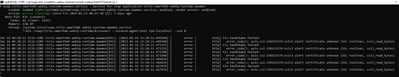
I can now reach the web application at the listener endpoint. In my case it is https://192.168.1.100:12345/cp_1/
The browser still displays a "Not Secure" tag and I see the error messages below in the service logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 08:37 AM
Bosch defined a request to implement TLS (https) communication in next WebIQ version 2.14
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 08:38 AM
The error messages in the log are correct, because the browser you're using tries to connect using SSL which has been disabled for security reasons in WebIQ a long time ago.
A browser will always display certificate warnings if you're not using an officially signed TLS certificate. Valid certificates must have these features:
- have a domain name rather than an IP address - especially not an internal IP address
- must not be self-signed
- must be signed by an accredited certification authority that is trusted by your browser vendor - if you have your own CA you can also add it for it to be trusted
- must not be valid for more than a year
Please note that all of this has nothing to do with WebIQ specifically and is the same for any webserver you would be using without any difference whatsoever. The certificate files are the same for any webserver like NGINX, Apache or WebIQ - there's really no difference.
So whenever you're having issues with the browser not trusting your certificate you should be able to find solutions on Google.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 08:39 AM
WebIQ already fully supports TLS, see https://www.smart-hmi.com/blog/faq-items/does-webiq-support-ssl-tls-encryption-for-encrypted-https-c... for details
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 09:07 AM
The issue is, that it currently needs user action, which is hard to implement and needs experiance on ctrlX.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 09:14 AM
Yes, in addition, TLS certificates should never be put inside an HMI project as that way they could very easily be stolen (i.e. copied) because anyone would be able to download both the certificate and private key from the server through the browser!
Also, as certificates are not bound to any HMI, but to the server (as a port can be used by a single application only on a system) they belong to the WebIQ Server (Runtime) and not to any specific HMI.
However, with the current implementation of WebIQ on ctrlX this is not really comfortable for a user, I agree.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 09:26 AM
@Sgilk Security issue demo:
The user could download your full certificate data through these URLs:
https://192.168.1.100:12345/cp_1/TLS/certificate.pem
https://192.168.1.100:12345/cp_1/TLS/private_key.pem
Solution
Put the certificate files into the .db directory - then these files will not be served and are not accessible from the browser:
/var/snap/ctrlx-smarthmi-webiq-runtime/current/.webiq/WebIQ Projects/cp_1/.db/certificate.pem
/var/snap/ctrlx-smarthmi-webiq-runtime/current/.webiq/WebIQ Projects/cp_1/.db/private_key.pem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 03:29 PM
SmartHMI is currently working on adaptions that WebIQ can use the reverse proxy server of the ctrlX.
With the reverse proxy server you can communicate via https to WebIQ. See article: HowTo-view-content-from-mutiple-webServers-in-one-web-page