FORUM CTRLX AUTOMATION
ctrlX World Partner Apps for ctrlX AUTOMATION
- ctrlX AUTOMATION Community
- Forum ctrlX AUTOMATION
- ctrlX IOT
- Re: Confused with the firewall application for NAT port forwarding
Confused with the firewall application for NAT port forwarding
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 01:38 PM
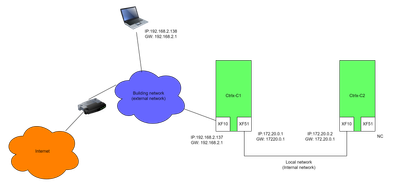
My usecase is pretty simple. I have an internal network onnected to XF-51 and an external network connected to XF-10
The internal is subnet 192.168.2.0/24 This network has devices with a web interface
The external subnet 192.168.100.0/24
I try to configure the firewall to port forward tcp (http) traffic from the external to the internal network. For instance incomming to the IP of XF-10 on port 8443 needs to be forwarded to 192.168.2.2 port 443
The confusion already starts from port naming shoudl it be XF-10, ETH0 or XF10. I think the latter is correct beacuse this is the name Linux reports.
I understand have to enable packet forwarding for both XF-10 & XF-51 which I did.
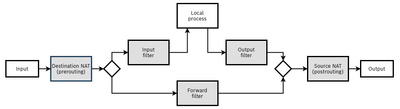
According the this diagram I need to configurer Dnat, forwarding and SNAT rules
Which seems to be a lot since I only have a few coonfiguration parameters to play with:
- Incomming interface XF10(??)
- Incomming protocol TCP
- Incomming port: 8443
- Destination interface XF51
- Destination IP: 192.68.2.2
- Destination port: 443
Al that information can go into the destination NAT
Is this correct? And if yes what should I put in the forwarding dan SNAT entries?
An example which uses OS 1.20 (new port names) is appriciated
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 03:56 PM
Hi @Marc_Smaak ,
If I understand your architecture correctly, you should only need to set SNAT rules and make a routing rule on the XF10 subnet devices.
You shouldn't need to match meta data oifname. It's redundant since you have seperate subnets on the interfaces.
Take a look at some of the How-Tos on this topic, specifically:
"How to use ctrlX CORE as a “router” using the Firewall App"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 04:50 PM - edited 03-22-2024 06:52 PM
@Sgilk Thank you for your reply. I have seen the post you mentioned but thought this is not exactly what I want since it is using the firwall as router while I want to use it as a NAT firewall. The diffrence is that for the client accesing the Webpage of a device behind the ctrlX it should simply think it comunicates to the ctrlx core IP address
Therefore this step should not be needed since this will not work in our usecase many diffrent PC will need to use this connection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 08:56 PM
I tested a bit more. Only if I configure a Destination NAT rule the ctrlX open a port. NMAP scan proves this, the browser response change from "connection refused' took 'took long to respond' So the massage is not corrcetly forwarded to the other network or the answer is not coming back.
Using Destination NAT makes sense since the desciption say port forwarding which is what I need.
I cannot help thinking this is far too complicated, iI need get this to work by Monday else I must advise my customer to use someting else e.g. a router running openwrt (3 minute task, just did it) Any tips??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 09:37 PM
Hi @Marc_Smaak ,
I believe at this point, you also need a SNAT rule to direct the response message.
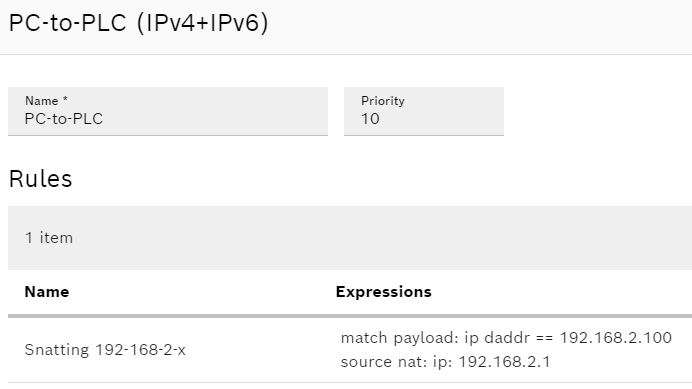
As an example, if I had a device on the internal subnet at 192.168.2.100 and the internal subnet adapter IP is 192.168.2.1, I would use the following rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2024 01:58 PM - edited 03-24-2024 02:06 PM
@Sgilk Thank you this indeed works.
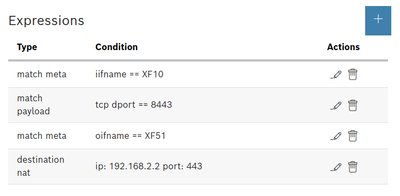
So for testing this is my setup
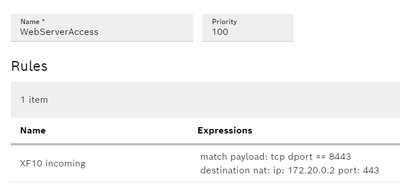
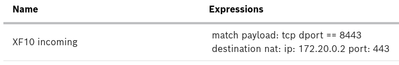
And these are my firewall rules:
Destination NAT
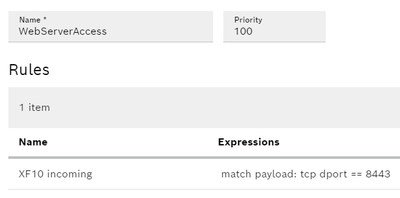
Which I beleive can even be simplified to
But I suspect this only works beacuse the traffic is https so defaults to port 443. If it would be another port I need to add the port info somewhere
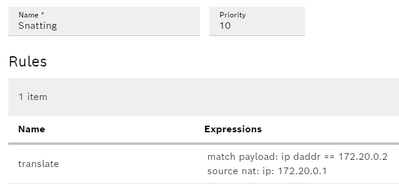
Source NAT
Also after a reboot (saving the firwall first) this all still works
Thanks at lot!!!
If you can explain better wat the Source net rule does this would be ewelcomed. I already worked with it but I thought it was intended for the return path to replace the source address of the device on my internal network (172.20.0.2) into the IP of the CtrlX core on the external network (192.168.2.137) This did not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2024 02:03 PM
On 2nd tought I think I get it. The Source IP address of my message towards the internal IP (172.20.0.2) would noramlly be the IP address of my laptop (192.168.2.138) With this rule it gets replaced with the IP of the ctrlX core on the internal network (172.20.0.1 ) Therfore the internal device just replies to 172.20.0.1 and does not need a Default gateway. Is this indeed the correct assumption?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2024 03:48 PM - edited 03-25-2024 02:13 PM
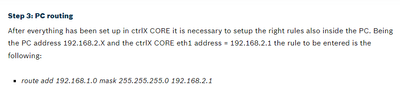
Exactly. I believe if you set the default gateway on the internal network devices to the ctrlX CORE internal network adapter IP, you should not need the SNAT rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2024 10:56 AM
@Sgilk wrote:
Exactly. If you set the default gateway on the internal network devices to the ctrlX CORE internal network adapter IP, you would not need the SNAT rule.
Strange, that is what I did as sown in the picture but it did not work. Will trey again later I am not at my system right now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 09:56 AM - edited 03-27-2024 10:03 AM
Tested again with only a DNAT rule and correct default gateway config and can confirm it is working. (I had a type in my default gateway)
So this is the only rule needed to make the conif of my picture working
This is how I started initially 😖
Just some clear examples for diffrent usecases would for sure help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2024 07:04 PM - edited 05-17-2024 07:26 PM
I thought I would also share my use case here and what worked for me for anyone trying to do something similiar.
I have a local network with multiple XM control. I am using the ctrlX as a NAT. I want to assign one IP address that is publicly available to a local address. In this case, when I login at 192.168.3.6 I should login to 192.168.1.2 and if I login at 192.168.3.7 then I should login to 192.168.1.5.
I am using the firewall app with rules set for DNAT and SNAT. Here I have no ports configured so that the address should act just as if the device was on the same network.
Here is the DNAT configuration:
and here is the SNAT configuration:
XM at 192.168.3.6:
XM at 192.168.3.7: