FORUM CTRLX AUTOMATION
ctrlX World Partner Apps for ctrlX AUTOMATION
Dear Community User! We have started the migration process.
This community is now in READ ONLY mode.
Read more: Important
information on the platform change.
- ctrlX AUTOMATION Community
- Forum ctrlX AUTOMATION
- ctrlX CORE
- "Self-signed certificate" error while using TLS certificates in MQTT connection
"Self-signed certificate" error while using TLS certificates in MQTT connection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2023 04:24 PM
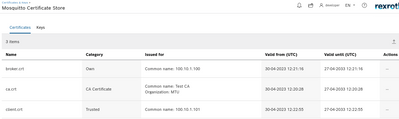
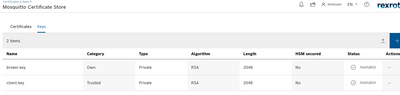
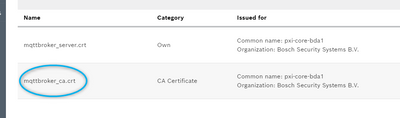
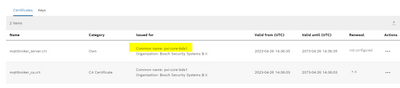
Some background: I am testing Cedalo MQTT broker connection using self-signed certificates on MQTT Explorer. I have generated SSL certificates using openssl on my Ubuntu machine and added them in both Mosquitto Certificate Store & MQTT Explorer as shown below.
Certificates in ctrlX CORE "Mosquitto Certificate Store"
Certificates in "MQTT Explorer"
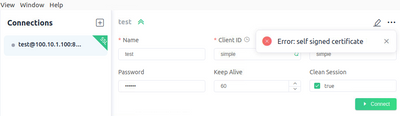
Issue: The client connection request shows "self signed certificate" error when I try to connect with broker using the above approach. I have tested the connection with python as well on my computer and it shows the same error.
Questions
- Is the above approach correct to connect the clients?
- Is there something I am missing?
- Will the communication work when I use certificates from a trusted source?
- Is there any example of connecting the broker in ctrlX CORE via self-signed certificates?
Any help would be appreciated.
Thanks
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2023 08:47 AM
We are also implementing certificate authenication for our own Mosquitto broker. I still find it is very easy to make an mistake so maybe some background to start with sorry if this is all clear.
The broker certificate is useful to allow clients to athenticate the broker before they send the acces credentials (mqtt user + password) I consider this the biggest tspe to get things more secure. Without this somebody can use the ctrlX-CORE Ip address on a diffrent device and easily steals the access credentials from the client.
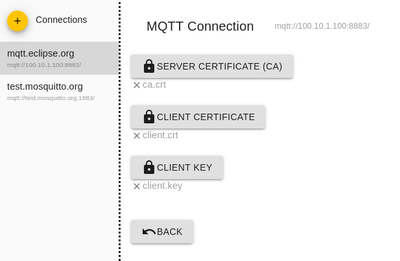
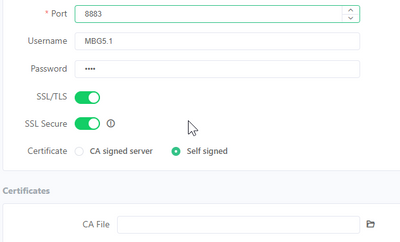
To allow the client to check the certificate it needs the root certificate from which the MQTT server certificate is created and signed. So if you use sefl signed you also need this 'CA' certificate and add it to MQTT explorer as CA certifiacte. The client certificate + key can be left blank (see below).
This allows MQTT explorer to validate thepublic key in the MQTT server certificate supplied by the MQTT broker.
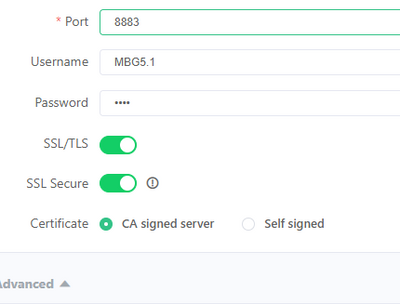
Alternatively you can use a formal CA signed certificate. e.g. letesencrypt for the MQTT broker. In that case there is no need to supply any certificate to MQTT explorer since it has access to the root certificates itself.
The GUI for MQTTX is a bit clearer on this point:
CA signed
And with self signed you get the option to add the CA certificate
Client certificate
The use of the client certificate is for authentication of the client by the broker. It avoids that rogue clients although they have the right access credentials can connect to your broker. For this you beed to generate a client certificate signed by the CA certificate of the MQTT broker. This again can be a selfsigned certifiacte or a CA sgned certificate. TH eprivate key for the client is only used on the client to prove this client is the legal owner of the certificate (p[ublic key) If this key gets into the wrong hands the client authentication is useless 😉
We are not using this yet. If you want to you need to generate a certificate signing request based on your private key. If your broker uses self signed this signing request needs to get processed by the ctrlX-CORE. I do not know excatly how that works with the certificate manager GUI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2023 05:02 PM
Hi,
Thanks for the response.
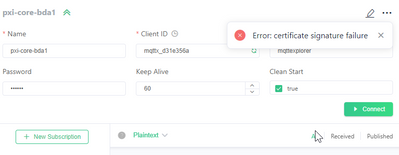
Sorry, but I could not fully understand how to use the self-signed certificate. I just installed the MQTTX software and tried to connect the client by selecting the "Self signed" option. I have tried to connect the client using just the CA certificate as well as CA+client cert+client key.
I am still getting the same error. Please see the attached figure below.
Is there any tutorial or working example to solve the issue? Also, I would be glad if you can share the steps you have followed in your solution.
Thanks a lot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2023 09:57 AM
So just to be clear you downloaded the CA for the certificate manager MQTT (As said we are using our own broker so I do not know the details)
Please check what is used as common name for the server certificate, we are using the hostname. You must use the same name to connect to the broker from the client.
Leave the client certificate and private key blank
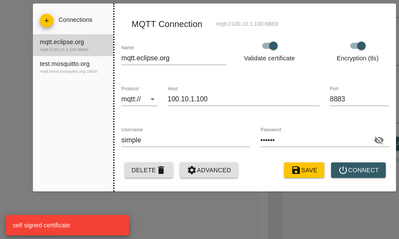
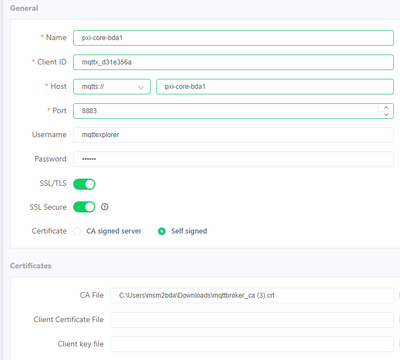
This is my full configuration which connect succesfully.
If I change the CA certificate or try to connect to a diffrent core I get which is intended.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2023 04:40 PM - edited 05-09-2023 05:21 PM
Since I wanted to know more about using cleint certificates I searched further and found this helpful explanation
http://www.steves-internet-guide.com/creating-and-using-client-certificates-with-mqtt-and-mosquitto/
For Mosquitto on the ctrlX this would mean:
- Get the MQTT CA certificate and coresponding private key ( currently we delete this key after generating the CA certificate 😉)
- Generate on a PC with open_SSL a private key for the client
- Generate with open _SSl een Certificate Signing request for this client private key
- Sign this with the CA certificate and CA pravate key
- Add the generated signed certificate and client private key to the MQTT client
- Configure mosquitto to use client authentication i.s.o. user/pass or both
For the record, I see I am a new member now but still the same Marc Smaak as from the reply's above 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2023 11:45 AM
Is this still an issue or can this topic be closed?