FORUM CTRLX AUTOMATION
ctrlX World Partner Apps for ctrlX AUTOMATION
- ctrlX AUTOMATION Community
- Forum ctrlX AUTOMATION
- SDK
- Re: Custom SNAP access to USB/Serial port "/dev/ttyACM0"
Custom SNAP access to USB/Serial port "/dev/ttyACM0"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 02:35 AM
Hello,
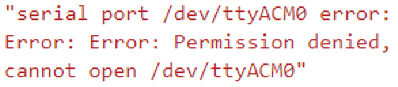
I need to access serial port using a custom snap without activating it via Node-RED to connect RS485 device with Serial to USB Adapter. As I understand, currently it's not possible without root privileges and in that case we are not allowed to use it in real project. Is it planned to add such rights in the future without granting root access to the device?
Thank you for your support!
Best Regards,
Alex
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 08:34 AM
Hello,
If you make a custom app the "serial-port" plug is what you need. Please try to make an app and see if the "serial-port" plug is connected. You can check it if you have SSH access with "sudo snap connections snapname".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2024 12:16 PM
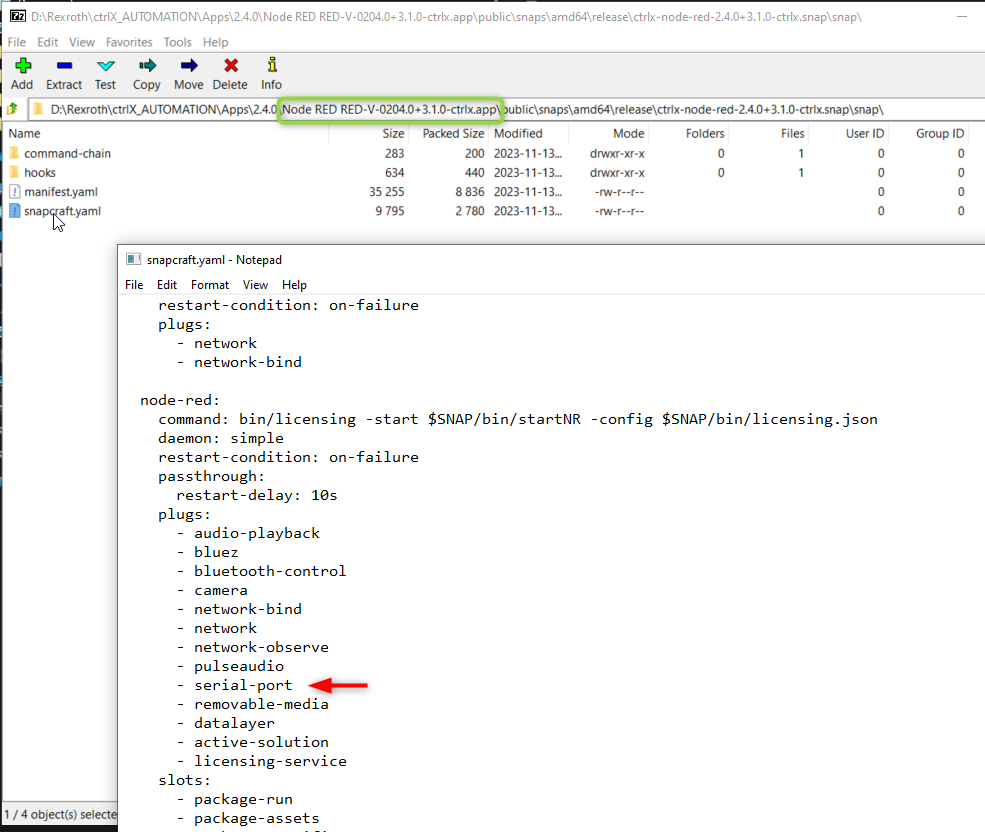
To follow up on Mauro's answer, I find it helpful to inspect (for example, using 7-zip) the snapcraft.yaml of existing snaps to see how the plugs are used:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2024 03:11 AM
Hello, finally could get back to this topic,
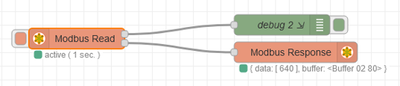
Can connect with Node-red and read registers from Modbus RTU slave. But no success with custom snap without root access, you need to connect raw-usb for that (need sudo), tried to bypass it by adding system-files interface, but it is also blocked by Ctrlx.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2024 12:45 PM
Hi @Akra
sorry, but I'm not sure if I understand you correctly. You want to access some device via USB. From Node-Red it works but from a self created snap it does not work, right?
Like @bostroemc mentioned you can look at the plugs which are connected to the Node-Red snap by unzipping it. Here you can see that the Node Red App uses the interface "serial-port". Therefor this should be also enough for your snap.
Best regards,
Nick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2024 03:50 PM
Just one more comment: As far as I know, daemons ALWAYS have root access within their area of confinement. (See, for example, comments by ogra here.) If you have configured your app to run as a daemon - the typcial use-case for ctrlX CORE - then access generally is a question of broadening the area of confinement via the plugs mechanism (i.e. setting up the plugs correctly) and never one of "sudo".