FORUM CTRLX AUTOMATION
ctrlX World Partner Apps for ctrlX AUTOMATION
Dear Community User! We have started the migration process.
This community is now in READ ONLY mode.
Read more: Important
information on the platform change.
- ctrlX AUTOMATION Community
- Forum ctrlX AUTOMATION
- ctrlX IOT
- Re: Connecting Node RED OPC UA Client with SmartFunctionKit Handling
Connecting Node RED OPC UA Client with SmartFunctionKit Handling
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 05:31 PM
Hello,
I'm trying to connect a CtrlX Core to another CtrlX Core with the SmartFunctionKit Handling application. SFK4H has an OPC UA server and I want to send Commands from another CtrlX Core with Node Red.
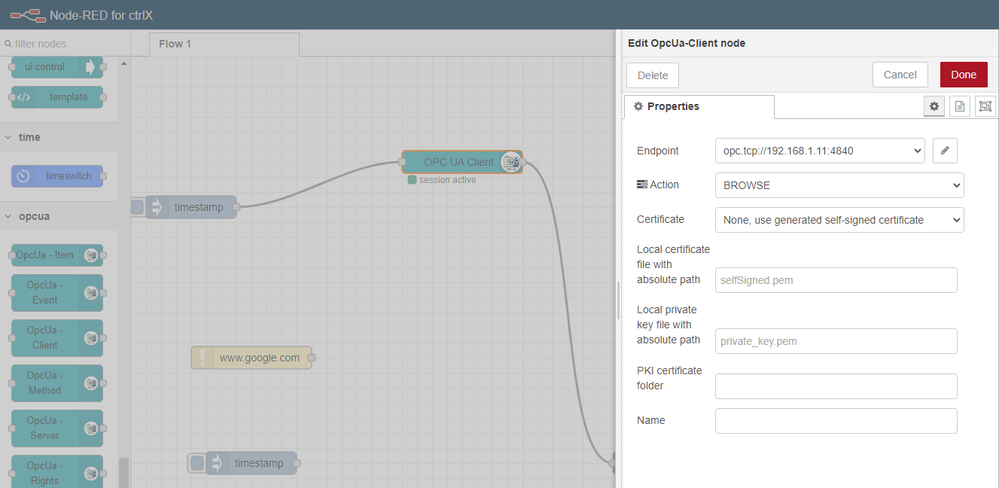
With the OPC UA Contrib palette and the OPC UA client node I have a certificate failure (Picture attached).
This same connection to a XM without security works perfectly.
I understand that I have to install some certificates in the CtrlX Core client, in the Certificates & Keys/Node Red?
I have to specify the path in the Node Red node (Picture 2)?.
A short guide to what certificates I need and where to store them could be provided.
Thanks in advance.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 11:04 AM
Provide your own Certificate Authority
!!!Using self-signed certificates is only recommended for test, not for production!!!
If you're client certificate is not selfs-signed, you have to
- Provide a CA with assigned Revocation List (RVL) and a derived client certificate from.
- Upload all of your CA- and intermediate certificates to the Node-RED PKI storage of the ctrlX as trusted certificates.
- If the CA specifies a Revokation List, upload the Revocation List to the UA Server PKI store of the ctrlX via UI (if supported) or manually using SSH (Root permissions required).
Prerequisites
Ensure openssl to be installed on the system and the path added to your environment path variable.
Ensure Node.js to be installed on the system. We recommend to use the latest LTS version.
Install node-opcua-pki
Intructions
- Generate batch out of following code:
::---------------------------------------------------------------------------------------------------------------------------------------------------------------- :: GENERATES A CA CERTIFICATE AND A DERIVED OR SELF-SIGNED CERTIFICATE FOR OPC UA USAGE (*.PEM FORMAT, INCLUDING PRIVATE KEYS) USING NODE-OPCUA-PKI AND OPENSSL ::---------------------------------------------------------------------------------------------------------------------------------------------------------------- @echo off ::https://github.com/node-opcua/node-opcua-pki ::setup ::-------------------------------------------------------- ::Create self-signed certificate enabled: 0/1 set CREATE_SELFSIGNED_ENABLED=1 set CRYPTO_SCRIPT_PATH=.\node_modules\node-opcua-pki\bin set CRYPTO_SCRIPT=node %CRYPTO_SCRIPT_PATH%\crypto_create_CA.js set CA_DIR=%CD%\CA set PKI_DIR=%CD%\PKI set CERT_DIR=%CD%\certs set KEYSIZE=2048 set VALIDITY_DAYS=3650 ::CA set CA_SUBJECT_NAME=xxxMyNamexxx set CA_SUBJECT=/C=DE/ST=xxxMyStatexxx/L=xxxMyTownxxx/O=xxxMyOrganisationxxx/CN=%CA_SUBJECT_NAME%/emailAddress=xxxMy@Mailadress.xxx set CA_CERT_PATH=%CA_DIR%\public\cacert.pem set KEY_PATH=%PKI_DIR%\own\private\private_key.pem ::client set CLIENT_SUBJECT_NAME=NodeOPCUA-Client@xxxMyHostNamexxx set CLIENT_KEY_PWD=xxxMyKeyPasswordxxx set CLIENT_SUBJECT=/C=DE/ST=xxxMyStatexxx/L=xxxMyTownxxx/O=xxxMyOrganisationxxx/CN=%CLIENT_SUBJECT_NAME%/emailAddress=xxxMy@Mailadress.xxx set CLIENT_APPLICATION_URI=urn:xxxMyHostNamexxx:NodeOPCUA-Client set CLIENT_CERT_NAME=%CLIENT_SUBJECT_NAME%.pem ::-------------------------------------------------------- echo GENERATES A CA CERTIFICATE AND A DERIVED OR SELF-SIGNED CERTIFICATE FOR OPC UA USAGE (*.PEM FORMAT, INCLUDING PRIVATE KEYS) USING NODE-OPCUA-PKI AND OPENSSL echo Please edit this script to setup, first! ::proceed? :again set /p answer=Proceed (Y/n)? if /i "%answer:~,1%" EQU "Y" goto proceed if /i "%answer:~,1%" EQU "n" goto end goto again1 :proceed ::echo initializing ... ::rmdir %PKI_DIR% /Q /S ::mkdir %PKI_DIR% ::rmdir %CA_DIR% /Q /S ::mkdir %CA_DIR% echo create certificate ... if %CREATE_SELFSIGNED_ENABLED%==1 ( %CRYPTO_SCRIPT% certificate --root=%CERT_DIR% --selfSigned --CAFolder="%CA_DIR%" --PKIFolder="%PKI_DIR%" --subject="%CLIENT_SUBJECT%" --validity=%VALIDITY_DAYS% --output="%CLIENT_CERT_NAME%" --applicationUri=%CLIENT_APPLICATION_URI% ) else ( %CRYPTO_SCRIPT% certificate --root=%CERT_DIR% --CAFolder="%CA_DIR%" --PKIFolder="%PKI_DIR%" --subject="%CLIENT_SUBJECT%" --validity=%VALIDITY_DAYS% --output="%CLIENT_CERT_NAME%" --applicationUri=%CLIENT_APPLICATION_URI% ) if %ERRORLEVEL% NEQ 0 ( goto error ) echo convert certificate to *.der format ... %CRYPTO_SCRIPT% toder "%CLIENT_CERT_NAME%" if %ERRORLEVEL% NEQ 0 ( goto error ) echo dump ... %CRYPTO_SCRIPT% dump "%CLIENT_CERT_NAME%" if %ERRORLEVEL% NEQ 0 ( goto error ) echo. echo fingerprint %CRYPTO_SCRIPT% fingerprint "%CLIENT_CERT_NAME%" if %ERRORLEVEL% NEQ 0 ( goto error ) echo. echo CA certificate echo %CA_CERT_PATH% echo. echo private key echo %KEY_PATH% echo. :end ::-------------------------------------- :: ERROR HANDLING ::-------------------------------------- ::echo %ERRORLEVEL% :success :: Success color A0 pause exit 0 :error :: Error color C0 pause exit /B %ERRORLEVEL% - Put the script to any folder
- Navigate to the folder
- Install here node-opcua-pki: npm install node-opcua-pki
- Edit the script (exchange all xxx...xxx)
- Execute the script
- Upload certificates via the WebUI of the ctrlX COREs (Settings -> Certificates & Keys -> Node-RED -> Certificates)
- They will end up on following locations:
- ca (certificate authority)
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/ca/certs/ - own
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/own/certs/ - trusted (other)
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/trusted/certs/
- ca (certificate authority)
- They will end up on following locations:
- Upload keys via the WebUI of the ctrlX COREs (Settings -> Certificates & Keys -> Node-RED -> Keys)
- They will end up on following locations:
- ca (certificate authority)
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/ca/keys/ - own
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/own/keys/ - trusted (other)
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/trusted/keys/
- ca (certificate authority)
- They will end up on following locations:
- Insert the full path to your certificates in Node-RED by using the given paths appending your certificate name. If your server-certificate is self-signed, uncheck "Check server certificate".
Node-RED OPC Ua certificate paths
- Deploy or restart the flow
- The OPC UA connection will be rejected at first time, because of untrusted server certificate.
- Trust certificates via ctrlX CORE WebUi, where OPC UA server is running (Settings -> Certificates & Keys -> OPC UA Server-> Certificates)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 11:23 AM
Hi David08,
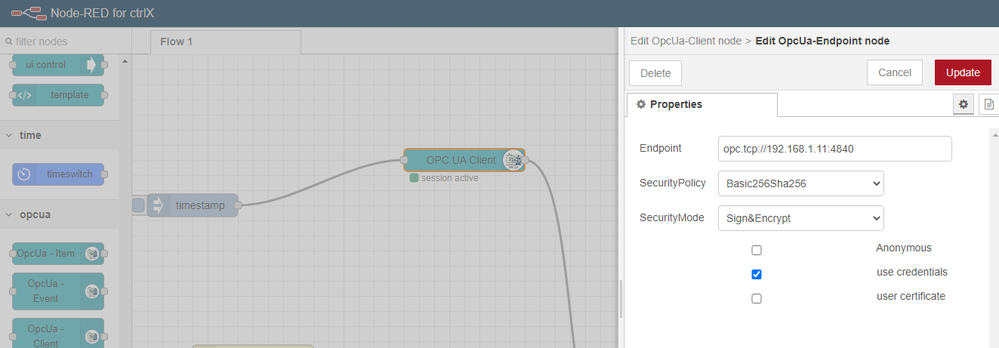
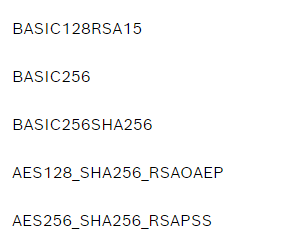
the settings in the screenshots work for me, you can select eg. "AES128_Sha256_RsaOaep" and "self-signed certificate".
Also other settings should work, plaease see other screenshot.
You need to trust the certificate in the ctrlX CORE where the server is running. Settings --> Certificates&Keys --> OPC UA Server
If you want to use your own certificates on client side you can store them via the web interface in Settings --> Certificates&Keys --> Node-RED .
Access from Node-RED is with this path possible:
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/own/certs/YOURcert.crt
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/own/private/YOURKey.pem
/var/snap/ctrlx-node-red/common/package-certificates/ctrlx-node-red/node-RED/ca/YOURCAcert.crt
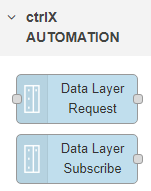
Alternatively you could use the ctrlX AUTOMATION Nodes to access the remote datalayer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 04:49 PM
Thanks CodeShepherd and TheCodeCaptain,
I have used the solution with Node Red CtrlX Automation Nodes. They work just like the OPC UA. I've done some tests with the certificate but it's a bit complicated for me and it didn't work for me. As I'm testing for a Demo I'm going to use the CtrlX Nodes.
Thank you very much for the quick reply to both of you