- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The Motivation
Production machines are really different one from the other but any machine has a controller (or more) that can be a target during a cyber attack. So how to protect our production? Just take outside some service that we need using a Port forwarding and then filter all the others. This solution is simple but usable with most of the devices.
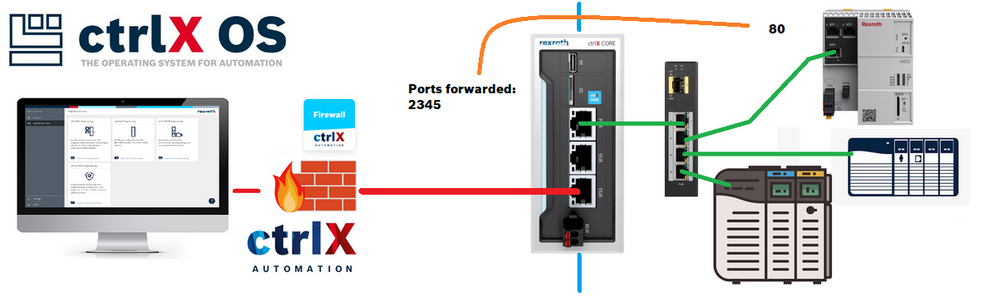
Overview of the used setup
The idea is to access devices that are locally accessible by the ctrlX CORE. For this tutorial we want to access an IndraControl XM22, as shown in the picture below.
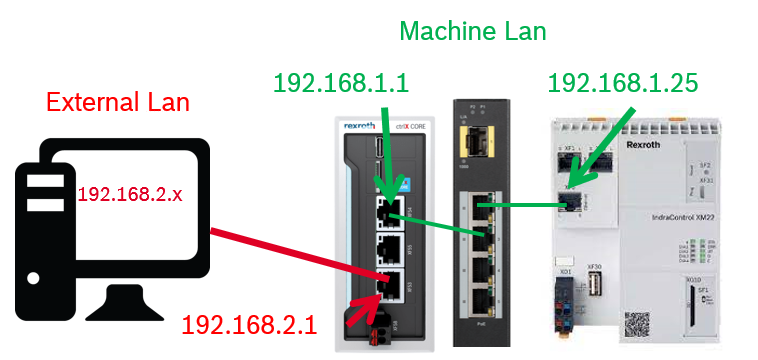
Equipment used
- ctrlX CORE installed system apps release 2.02
- XF10 set to 192.168.1.1, XF51 set to: 192.168.2.1
- ctrlX AUTOMATION - Firewall app 2.02 (not working for 1.20)
- IndraControl XM22 as target device in the network
Transfer data packets
Step 1: Forward data packets
In order to forward data packets it is necessary to allow IP forwarding between XF10 and XF51 interfaces:
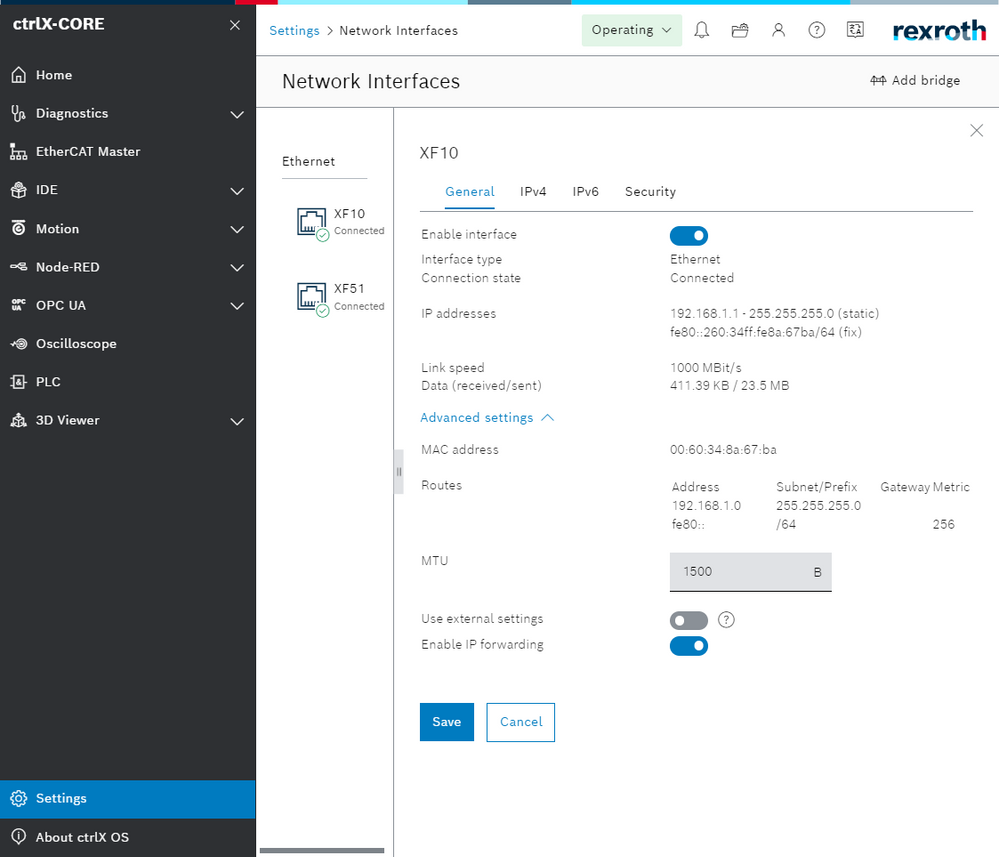
From firewall point of view it is also necessary to allow the packet forwarding (by default it is allowed). Then we will restrict it in order to select which package has to run.
Step 2: DNAT and MASQUERADING Settings
Now we have to setup the ctrlX CORE so that once we're interacting with the port 8082 of it we're in fact getting in contact with port 80 of the XM22. To achieve that we need to first access the firewall app and add a chain in the DNAT section if not present.
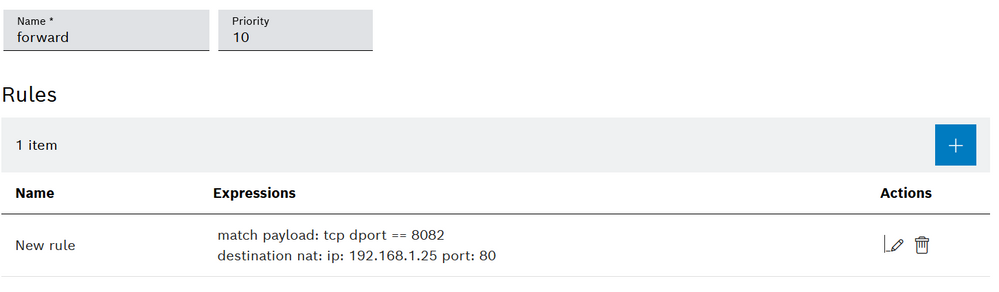
Once we have created the chain we have to edit it and add a rule: any TCP request on port 8082 will be "DNATted" to port 80 of 192.168.1.25 so we have to match any packet over TCP protocol with destination port 8082.
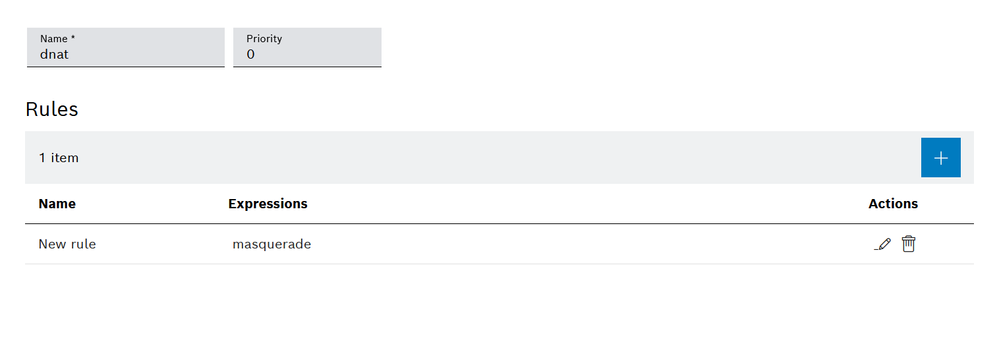
Now we have to fix the packets that are coming back using a masquerade directive. To achieve that we add a chain on the SNAT section and a rule containing the MASQUERADE directive.
Step 4: XM22 access
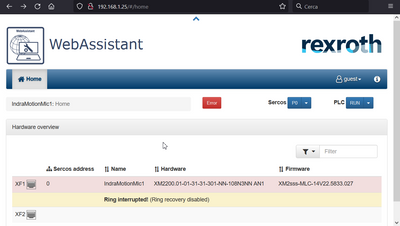
Now it is all set up! When entering http://192.168.2.1:8082 to the browser the XM22 WebAssistant page should be reachable!
Step 4: PROTECT the controller blocking all the ports and then allow just what we need to use
Please refer to: Cybersecurity: use ctrlX CORE as a powerful net-filter for any controller!

You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.