- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How-to enable TLS secured Remote Logging connection in ctrlX OS 1.20
In ctrlX OS 1.20, TLS configurations can be configured via configuration file, only. The frontend does not yet provide the option to create connections to endpoints with TLS verification. This document describes the required steps to setup a remote logging configuration via "Manage App Data" and configuration files.
Please note the current limitations and known issues.
Please see also actual XCR-V-0120 documentation (without TLS): Diagnosis / Remote Logging
Configuration files
filters.json
[
{
"Id": "000d2c60-6ac8-4601-a8ef-2fd599de7b7b",
"FiltersCfg": []
}
]>div<Please note that the file must be named filters.json. The ID may be choosen freely, but must be unique.
targets.json
[
{
"id": "000d2c60-6ac8-4601-a8ef-2fd599de7b7b",
"name": "testtls",
"url": "tls://10.0.2.2:55999",
"enabled": true,
"tag": "empty",
"messageFormat": "RFC5424",
"messageFramer": "none",
"tlsConfig": {
"certificate": "client-vir-cert.pem",
"key": "client-vir-key.pem",
"ca": "ca-cert.pem",
"skipServerCertificateVerification": false
}
}
]Please note that
- The file must be named targets.json.
- The ID must be identical to the ID in filters.json.
- The URL ("url") must start with the prefix "tls://".
- The certificate, key and ca certificate ("certificate", "key", "ca" under "tlsConfig") must be located in the certificate store "Network security" and must be named as stated in the configuration file. Depending on the use case, not all files are required. Please refer to the installation steps as described below for further details.
Installation Steps (Keys & certificates)
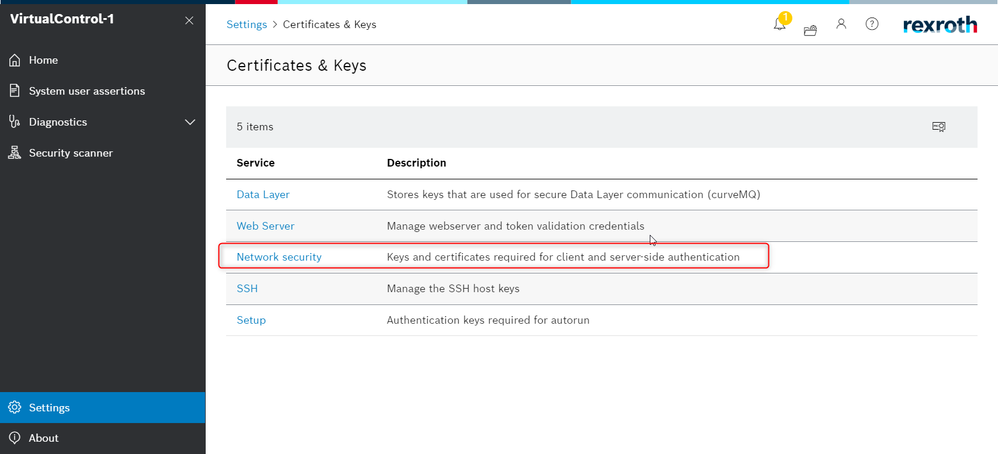
If either the server certificate shall be verified and/or the client must authenticate against the server, the required files must be made available in the certificate store "Network security" in the certificate management:
Use Case: Server Verification only
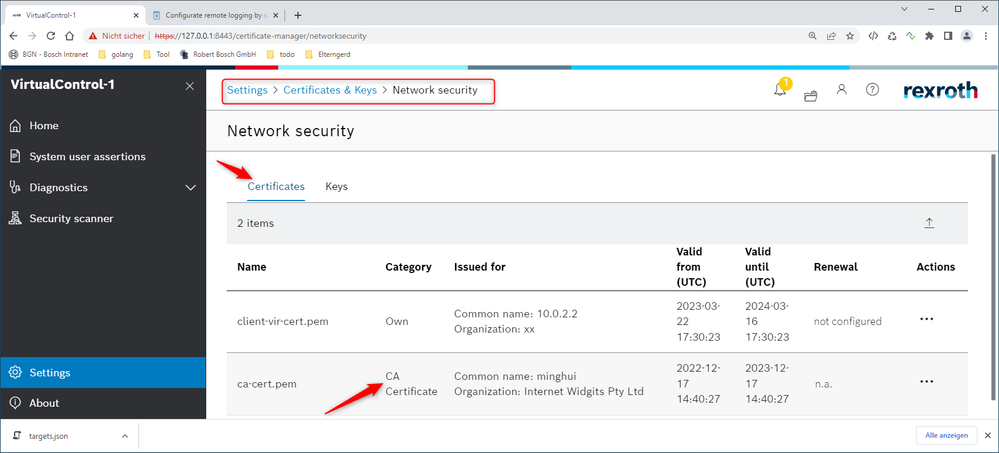
For the verification of the server certificate, the ca certificate file must be stored in the certificate store "Network Security" as a "ca" certificate. Please ensure that the name of the file is identical to the one stated in targets.json.
Use Case: Mutual authentication
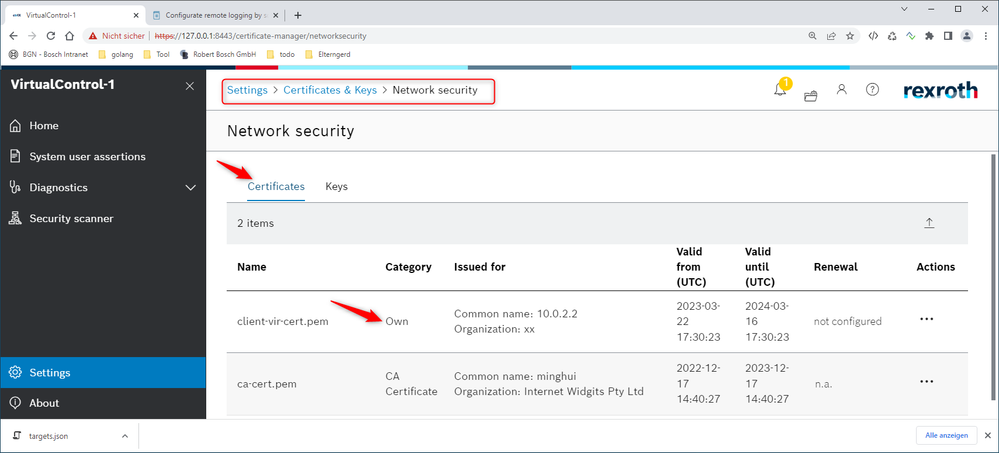
If additionally the remote logging server requires client authentication, the client certificate file must be made available as "own" certificate in the certificate store "Network Security" in the certificate manager. The client private key file needs to be made available as "own" key in the certificate store "Network Security" in the certificate manager. Please ensure that the names of the files are identical to the ones stated in targets.json.
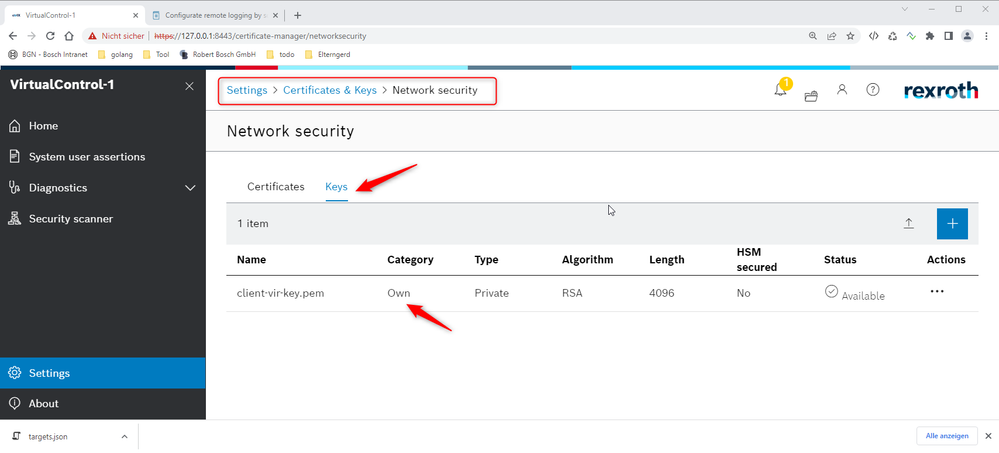
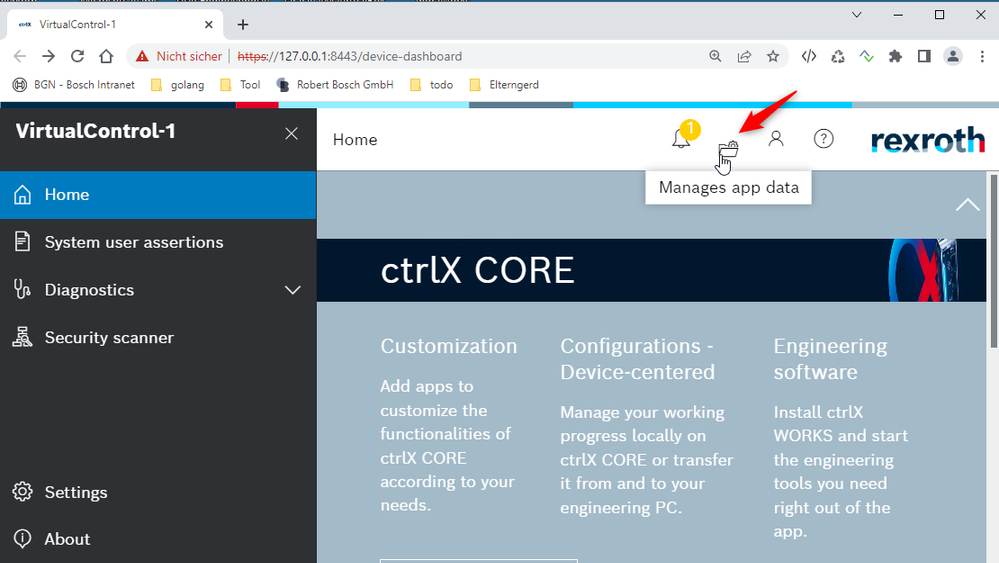
Upload the configuration (filters.json, targets.json)
1: Open "Manages app data"
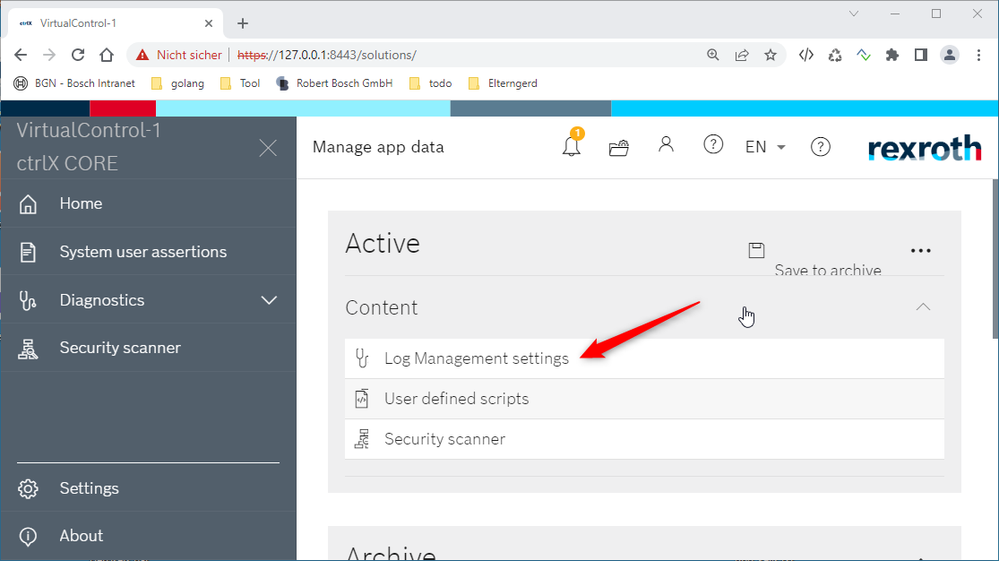
2: Go to "Log Management settings":
3: Upload filters.json and targets.json
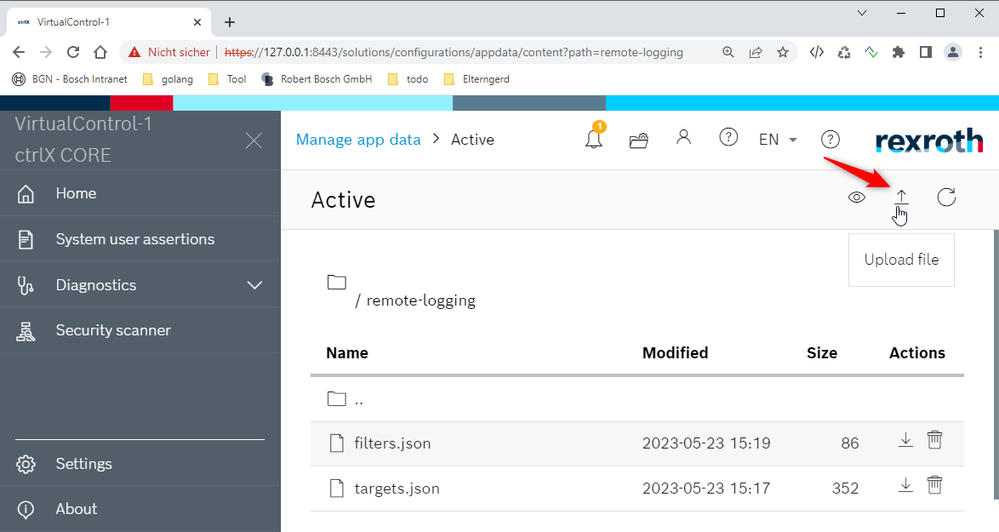
Or modify existing filters.json and targets.json. Then "Save" the settings.
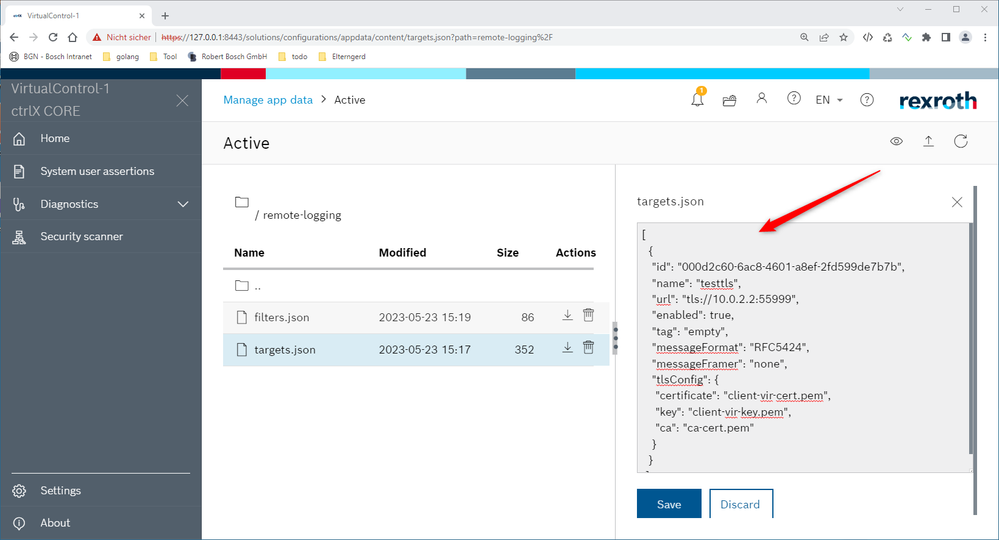
4: Restart device
For the settings to take effect, the device must be restarted.
Known issues / limitations
- TLS configurations are displayed in the UI, but cannot be modified.
- A restart of the device is required for the settings to take effect.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.